Cybersecurity for Industrial Processes
Cybersecurity has become an increasingly prevalent subject in the last decades. While the focus has been largely on IT infrastructure and online safety, more attention has now been placed on Cybersecurity for industrial processes such as factory automation, water/wastewater plants, power generation and power T&D. This can be attributed to the increased awareness that cybersecurity required for IT is very different from cybersecurity efforts needed for industrial processes.
The main difference is the priority for these two information infrastructure. In IT, it is possible to focus heavily on cybersecurity, such that emails, applications, documents can be blocked with minimal impact on a companies’ P&L. On the other hand, downtime can result if files are stopped from being passed from one device to the other for Industrial processes. Downtime for Industrial processes is very costly as one can observe below.
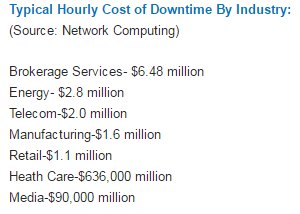
The are explicit costs due to downtime. In the case of concerted attack on Nuclear Power Plans (stuxnet incident) or Power T&D systems (recent Ukraine cyberattack, causing mass blackout affecting at least 200,000 citizens), prolong system downtime can lead to life being lost, severe inconveniences amongst other non-monetary, immeasurable outcomes.
With such different requirements, it is then common sense that plant owners should look beyond IT cybersecurity devices for protection of industrial processes. While firewalls, VPNs, VLans, subnet etc. works for both IT and Industrial processes; IDS/IPS (Intrusion detection system/Intrusion protection system) is not ideal for Industrial processes because they are actively monitoring the data passing through. This not only slows down data transfer and cause delays (again, not damaging in IT network) but often results in false alarms: There can be unusual data passing through which might not be malicious but are essential to operations. IPS/IDS will stop these data and can potentially lead to down time.
In particular, IPS/IDS are used to protect against zero-day attacks/advanced persistent threats where an external party remains in contact with malicious code after they infiltrate systems. These external parties then manipulate these codes further to target specific loopholes. As such, anti-virus cannot detect these codes (no known signature) and firewalls/VPNs are bypassed.
At Phoenix Contact, we recommend MGuard with CIFS Integrity Monitoring that is tailored for Industrial Processes Protection against Zero-day attacks and advanced persistent threats:
Discover Malware on Day Zero: Integrity Monitoring
Due to the general problems with the deployment of antivirus software on industrial PCs and the timely provision of malware signatures, alternative techniques of integrity assurance are gaining relevance for the protection of industrial systems.
One solution is the CIFS Integrity Monitoring feature offered on Phoenix Contact’s FL mGuard security devices. CIFS, or Common Internet File System, is a file-sharing protocol used by Windows and other operating systems. Viewing files on network file servers and using shared network drives are common activities that utilize CIFS. With Integrity Monitoring, the user can monitor configurable sets of files for unexpected modifications of executable code. When initialized, Integrity Monitoring computes a baseline of signatures for all monitored objects and then periodically checks them for any deviations. This process works without any external supply of virus signatures, without the risk of disrupting operations through “false positives,” without installation of software, and with only a moderate load on the monitored PCs, while primarily utilizing the resources of an mGuard security appliance. The mGuard thus discovers suspect file modifications promptly, and reports them via SNMP and e-mail to network
management systems or responsible administrators.
In a test study performed at the University of Ostwestfalen-Lippe in Lemgo, Germany, researchers from the independent inIT institute for industrial IT (www.hs-owl.de/init/en/) have been able to verify that mGuard CIFS Integrity Monitoring would have recognized infections with Stuxnet on day zero as unexpected manipulations and warned asset operators against it long before any antivirus product. The device drivers installed by Stuxnet, as well as the modifications performed by the worm on the pivotal SIMATIC Manager DLL,
would have been discovered in the process.
Some other features that makes mGuard ideal:
- Stealth mode – fast retrofitting without the need to configure/reconfigure IP addresses
- OPC Inspectors – ability to track random ports opened by OPC Classic, which render firewall useless
- 3G remote access
- If there are deviations detected with CIFS integrity monitoring, SMS alarm can be sent to system engineers.
- Although regular CIFS scan can be scheduled, in the event of known cyberattacks, engineers can simply SMS into mGuard to start an adhoc scan
- With 3G, mGuard or devices connected to mGuard can be remotely accessed from anywhere around the world
To find out more about how mGuard can help to secure your industrial systems:
Click here to download a white paper on Post-stuxnet Industrial Security
or contact us at marketing@phoenixcontact.com.sg for a demo on MGuard configuration.