Urgent need for action for all stakeholders
The EU Cybersecurity Strategy, published in December 2020, focuses on resilience and attack blocking for major manufacturing companies. The strategy aims to implement security by design in products and systems, addressing the increasing attack area for cyberattacks and the increasing professionalism of attackers. Cyber security focuses on securing a company’s value creation and individual security objectives, including protecting know-how and complying with legal regulations. Significantly, the EU is now extending legal requirements for cybersecurity to include more companies.

Implementation in the automation sector
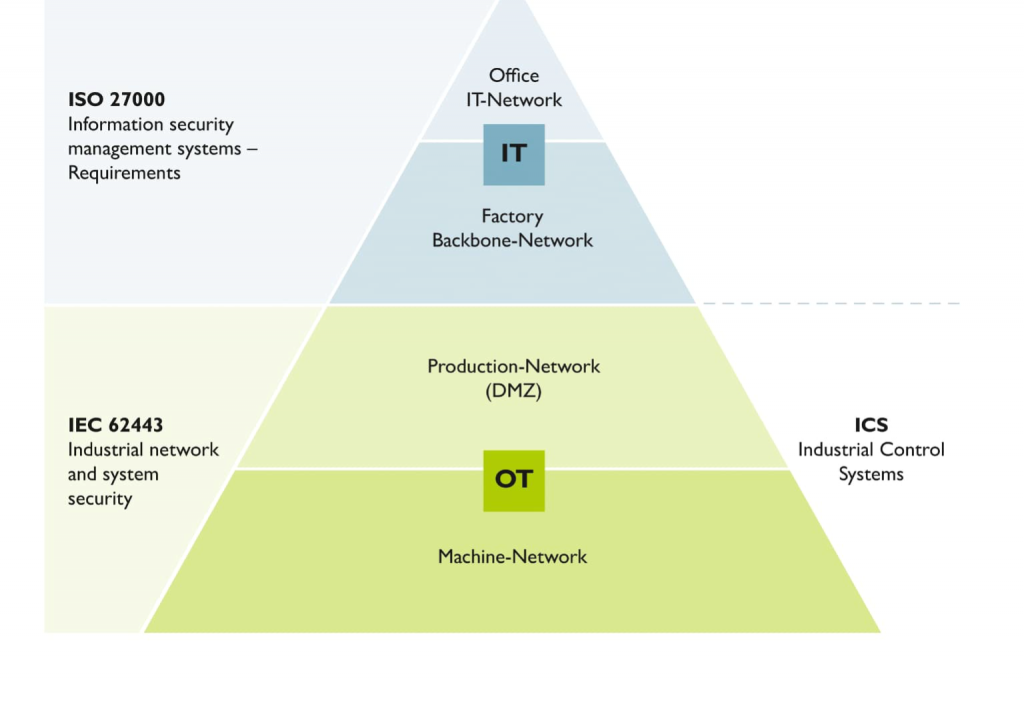
Based on ISO 27001/2, the information security management system (ISMS) in IT is being extended to operational technology (OT). Measures in the IACS environment can be applied by incorporating organizational and technical criteria, as part of this expansion. These measures include network configuration, data protection, user authentication, monitoring, device security hardening, and system management. The IEC 62443 series of standards addresses specific measures for the IACS environment, covering components, systems, operators, and service providers. The comprehensive security-by-design approach, known as the “defense-in-depth” concept, makes access more difficult for attackers.
Upvaluation of regulations through NIS 2
The EU’s NIS 2 directive, mandating cybersecurity measures for public and private entities, is changing the landscape. Specifically, it applies to companies with over 50 employees and more than 10 million euros in sales, focusing on essential and important facilities. Commencing from January 16, 2023, this directive must be transferred into national law by October 18, 2024. However, implementing security-by-design in products is challenging, and the EU has introduced the Cyber Resilience Act (CRA) to address this issue.
Development of security-by-design products in accordance with the Cyber Resilience Act
The Cyber Resilience Act (CRA) mandates manufacturers to create security-by-design products, ensuring they receive a CE mark if they comply with regulations. Minimum security measures must be demonstrated through conformity tests or manufacturers themselves using a harmonized standard. The CRA includes access protection, confidentiality protection, integrity, availability, and a secure delivery state. It also includes vulnerability management and regulations for manufacturers to provide security updates. The draft text of the CRA is in trialogue, expected to become EU law in 2024. To meet vulnerability management requirements, products must have a standardized Software Bill of Material and known vulnerabilities must be available in a standardized digital format.
Consideration of security in the new Machinery Directive
The Machinery Directive 2006/42/EC mandates machines to be equipped with functional safety technology, ensuring the protection of people and the environment from injuries or contamination. However, this standard requires updates due to new technologies and product safety regulations. Looking ahead, the Machinery Directive 2023/1230, set to be published by mid-2023, combines functional safety with cybersecurity.
360-degree security based on IEC 62443
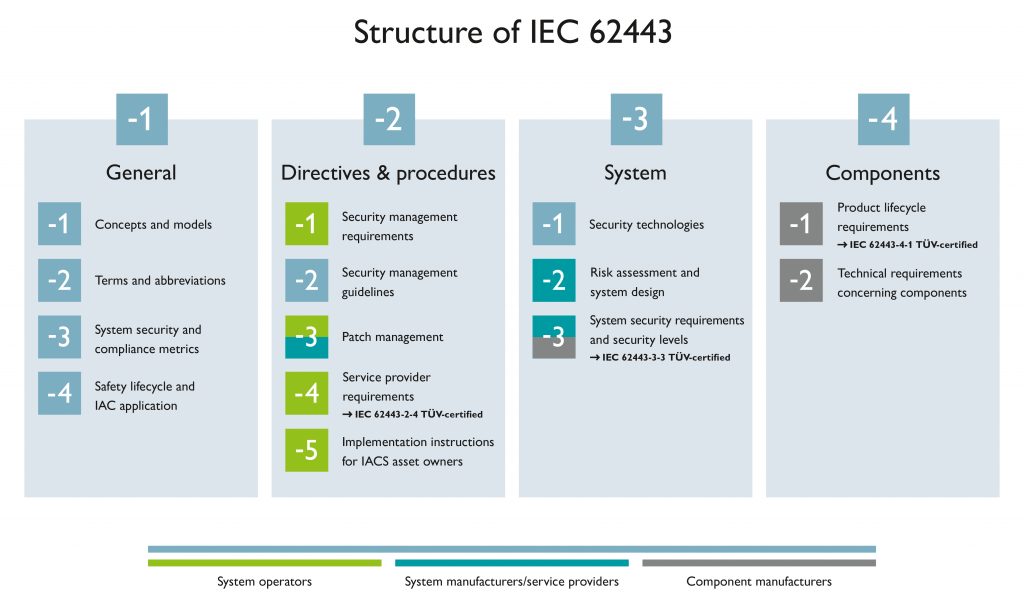
Phoenix Contact, a German company, has implemented IEC 62443 since 2017. In this time frame, it has focused on a 360-degree security concept throughout its products and solutions. The company follows a secure development process, ensuring security-by-design and defense-in-depth. Additionally, It actively monitors vulnerabilities and provides regular security updates. Moreover, the company’s secure products comply with IEC 62443-4-1 and IEC 62443-4-2, including denial-of-service protection, user management, and data confidentiality. Furthermore, the company’s security services are certified by IEC 62443-2-4. The Phoenix Contact Security Team has developed templates for various solutions and markets, and the Product Security Incidence Response Team (PSIRT) manages security issues. Importantly, all certifications are monitored by TÜV Süd through annual audits.
Learn more about Industrial security.

