Cloud computing is becoming increasingly popular as more and more companies use its services to store their data. The following article outlines the important considerations:
Traditionally, IT fields are outsourcing services to the cloud rapidly. It is better to opt for external services to an in-house team for a cloud-first strategy. Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS) are three types of cloud services, with industrial cloud services focused on applications.
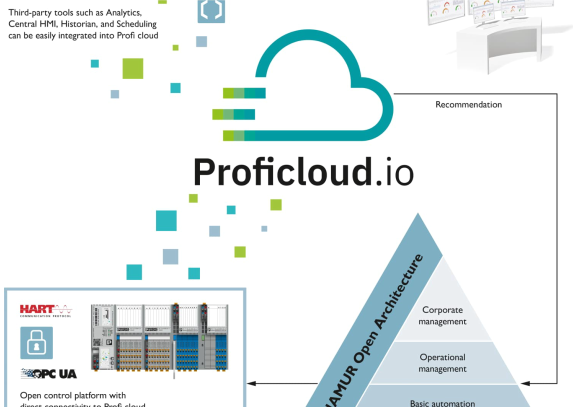
IT departments frequently use cloud services centered on specific use cases utilized by the whole organization. Industrial cloud services are of decentralized design. We observe a more detailed overview of an automation system consisting of components from many suppliers that will use various cloud solution features. Furthermore, it is important to determine the issue of how to handle such an idea. The use of industrial cloud services thus calls for a methodical strategy.
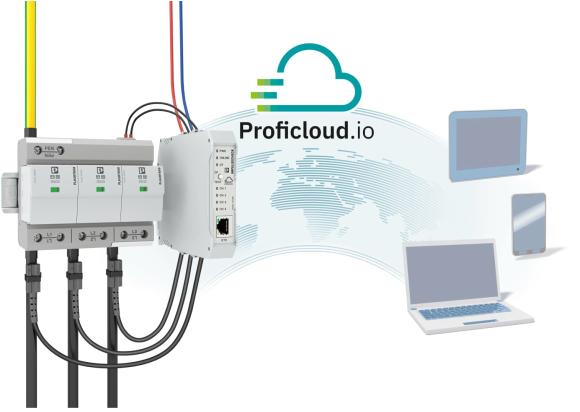
The interaction between field equipment and the offered services gives industrial cloud services their value (SaaS). This form of communication requires transfer of data between these two end points. Furthermore, It is theoretically feasible to establish a communication connection between the field device installed in the automation system and the cloud service.
An alternative is to utilize a cloud gateway that combines the communication connection from one or more field devices to the cloud service. This leads to a variety of connection solutions because of the different services available.
As a result, a condition monitoring program that uses one-way data transfer to monitor the state of a machine or component will need to be set up differently from, a remote maintenance connection.
Different threats
Different dangers are present in each of the many application scenarios. There is a chance that a one-way transfer of information from the field to the cloud might unintentionally become accessible. Hence, the field device acquires more more information than allowed.
Possibly intercepting data transfer prevents storage information disclosure. In this instance, altering the data would impact how it has been used in the cloud service but would not immediately affect the operation in the field.
Additional hazards arise because data or commands may be tampered with which may potentially cause damage at the field level. Another possibility for the attacker is performing an ad-hoc alteration at the field level, maybe outside a maintenance window.
No control with direct encryption
There are several ways to combat the threats mentioned. However, it is essential to take the cloud service into account. What data is being used? What services should I use? Can the communication occur across the business network or does it require a dedicated connection?
Assess the security features of the cloud service and the related provider: Are you operating the service using a secure development procedure? Do you have a security management system? The examination must also consider the security of the underlying platform and infrastructure.
encrypting Internet-based communication interactions is automatic. This strategy protects the data by safeguarding any simultaneous communications between the IDs, passwords, and access tokens. The lack of control by the operator over the connection creates an obstacle for directly encrypted connections between field devices and the cloud.
This situation is generally tolerable provided the required level of confidence can be established between the contractual parties as part of the security assessment and if the operator can set up the field device appropriately.
Example application scenarios
Below are some examples of industrial cloud services and how to secure them:
Cloud gateway
The gateway’s operator has control over data gathering, local processing, and subsequent transmission. The cloud gateway also relieves and decouples the field devices in this manner. The NAMUR international organization has specified a security gateway for the process industry sector in its suggestion 177 (1), which, because of its technological attributes, guarantees that the monitoring application has no bearing on the field level.
Monitoring levels of wear
When activated, the protective device is susceptible to wear, therefore, condition monitoring replaces it in a timely manner. Cloud gateway reads out the impact-free data.
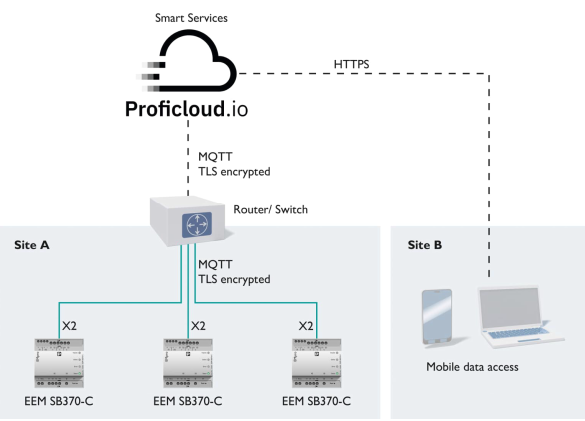
Energy monitoring
An energy monitoring system that does not require the maximum level of secrecy may gather and analyze large amounts of data, making use of a cloud service possible. The measuring devices capture the energy data and send it via the one-direction MQTT protocol to the cloud service (Message Queuing Telemetry Transport). The user can review and call it up there.
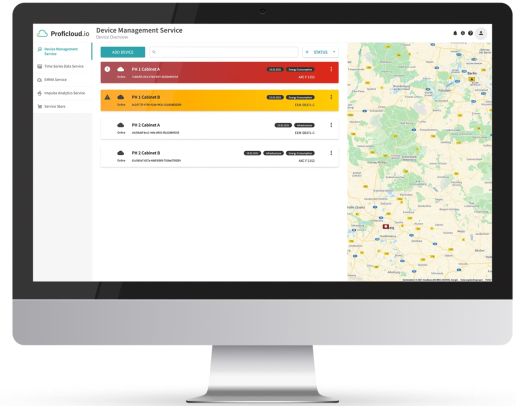
Device management
The security increases to actively regulate the field device using the device management system. Therefore, assess the security needs before using a cloud service.